| 15 min read
What is Zero Trust?
What's the difference between Zero Trust and perimeter security? We explore the benefits and limitations of both solutions, so you can find the best fit for your business.
What is perimeter security?
A network perimeter represents the boundary between an organisation's internal network (trusted zone) and external network (untrusted zone). It's where data flows in and out. Traditionally, this boundary was physical (firewalls at network edge). However, with cloud services and remote access, this concept has evolved.
Perimeter security is based on the simple concept of blocking anything from getting in, and a common metaphor used is like castle and moat. Everyone outside is a threat, everyone inside is trusted. However, once an attacker is inside the walls, perimeter security, by design, simply cannot respond.
What is Zero Trust?
Traditional security systems employing perimeter security are being placed under exponential strain by the simple fact that networks are becoming more diversified, and companies' data is being stored in more than one place, often due to the usage of cloud-based applications, as well as cloud-based redundancy for critical systems.
In order to cope with changing network access models, security systems have had to adapt to a concept that "all devices and applications that connect to servers and internal networks are potential threats, and should be treated as untrusted". Below, we've summarised the key principles and characteristics of Zero Trust:
Trust is never assumed - whether inside or outside the network, a user or service must continuously prove their identity, regardless how often a service is used or how secure it may be.
Zero Trust follows the principle of 'need to know'. Users and devices only get access to what they absolutely require. Much like physical rooms, you only get the key to the door you need, not the entire building.
Every device trying to access resources undergoes double checks, with Zero Trust verifying both who you are (user identity) and what you're using (device identity). MFA adds an additional layer on top of this - even if one factor fails, the other keeps the door locked.
Zero Trust divides the network into smaller zones called segments. Each segment has its own security rules, preventing attackers from moving freely within the network. By limiting access and segmenting users, many more roadblocks are created. While certain segments may become compromised, this reduces the speed at which attackers may gain access to an entire network.
KEY FEATURE #1
An emphasis on endpoint security
Endpoints (physical devices that connect to, and exchange information with a computer network) are a key aspect to Zero Trust, and aim to prevent attackers at the first hurdle. Endpoint security centres on the management and authentication mechanisms of connected devices, and can:
- Only enable authenticated devices to connect to a network
- Disconnect the connection immediately if an abnormal connection is detected
- Remove malware from infected devices
These capabilities are realised through a solution known as EDR (Endpoint Detection Response). With the recent proliferation of remote working and mobile work devices, EDR solutions are becoming increasingly essential.
KEY FEATURE #2
Moving security to the cloud
Cloud-based security in Zero Trust includes security using Identity Access Management (IAM), which can manage connection authentication and access restrictions as introduced in the Zero Trust network, as well as security monitoring and access restrictions to the cloud service itself.
Improper configuration of cloud services can lead to data leakage, account takeovers, and the connection of unwanted third party applications. In order to strengthen cloud security management, administrators need to have a birds-eye view of, and control over, a large number of cloud services. Cloud Security Posture Management (CSPM) responds to these challenges, by continously checking services for misconfigurations and violations of guidelines to improve consistency and control.
Introducing Zscaler's CSPM
CSPM, developed by Zscaler, enables users to:
CSPM automatically identifies and corrects SaaS, IaaS and PaaS application misconfigurations to ensure compliance, while also helping prevent cloud misconfigurations and providing unified visibility and automated remediation.
In an era where service providers are offering attractive cloud solutions at low costs, a configuration that relies on a single cloud service is far from ideal from an availability and resiliency perspective. CSPM can automate management that would take an enormous amount of time to do manually, which as an issue that scales exponentially in multi-cloud environments.
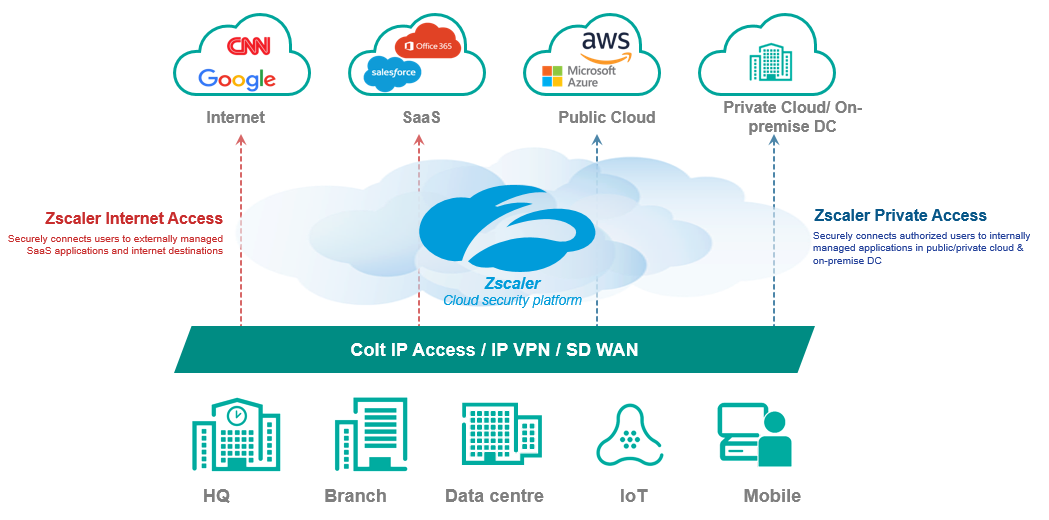
We've partnered with Zscler to provide a Secure Web Gateway service, available as an addition to our Direct Internet Access, IP VPN and SD-WAN services, enabling all network traffic routes through Zscaler, where security policies are applied & managed by the end customer.
Instead of having a stack of security and network appliances such as Firewalls, load-balancers, DDoS protection, IDPs etc. on premise, all of these appliances are instead in the Zscaler cloud, enabling you to easily scale protection to all offices and users, regardless of location, easily categories and apply security policies, and to minimise network and appliance infrastructure cost.
Secure Web Gateway
Colt has partnered with Zscaler to bundle their security solution alongside our networking products, adding any solution from the Zscaler security stack as an add-on to your services, and Colt can be your single point of contact across both services.
KEY FEATURE #3
Automated surveillance
In order to carry out detailed authentication, log collection, monitoring etc., it is extremely difficult (and increasingly expensive) to secure in-house IT or security resources, especially personnel. Many tasks ensuring good security practice are standardised to some extent, so they can be automated and streamlined.
One possible method is to use a SOAR solution. SOAR stands for Security Orchestration, Automation and Response. SOAR solutions automatically prevent and eliminate fraud, manage incidents and related tasks, allowing you to better manage tasks and workflows performed by help desks and security departments, and making recording and documentation far more streamlined.

Stay secure beyond borders
With employees working remotely and critical systens moving to the cloud, traditional network perimeters have exploded, and businesses need to stay secure beyond borders to enable success. To help you navigate this changing landscape, download our guide to effective SASE implementation.
The future outlook of perimeter security
The global perimeter security market is projected to grow at a compount annual growth rate of 6.1-10.3%, reaching a value of £124.5 billion by 2032. This growth is driven by the increasing need for perimeter security systems, with the growth in adoption of AI, ML and IoT technologies. Future trends in perimeter security include more advanced video analytics and increased collaboration between technologies.
Cloud-based security measures are becoming increasingly important as businesses continue to migrate to cloud environments. Gartner predicts that by 2027, 80% of vendors will offer cloud security posture management as a feature of their cloud security platforms, up from 50% in 2022. The Cloud Security Alliance has launched the industry's first authoritative Zero Trust training and credential, the Certificate of Competence in Zero Trust (CCZT), indicating the growing importance of zero trust strategies.
Due to the shortcomings of standard perimeter security as mentioned in this article, it is likely that cloud-based Zero Trust security solutions are likely to become more prominent as time goes on.
What's next?
How successful SASE frameworks drive network security
SASE is a cloud based framework that seamlessly integrates SD-WANs and Zero Trust security solutions, a next iteration of network security that mitigates security concerns associated with local breakouts & numerous network access points by de-centralising network security.
Expert's guide to SD-WAN implementation
Secure SD-WAN is fastly becoming organisations number one choice for delivering the benefits of local breakouts without the restrictions of on-premise security complexity. With an SD-WAN, you can configure your network in detail and in accordance with application priorities and network demand in real-time.
Optimise your critical bandwidth with local breakouts
As hybrid working and the use of cloud-based applications continues to drive network complexity, many organisations look towards local internet breakouts to help mitigate network congestion, reduce bandwidth requirements, and save costs while maintaining performance.
Secure Web Gateway with Zscaler
Colt has partnered with Zscaler to bundle their security solution alongside our networking products, adding any solution from the Zscaler security stack as an add-on to your services, and Colt can be your single point of contact across both services. Find out more about integrating your networking and security provider today.
